Phishing is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information such as credit card numbers, bank information or passwords. This is generally done on fake websites that look and feel legitimate. Cybercriminals typically pretend to be reputable companies, friends or colleagues in a fake message which contains a link to a phishing website.
When entering the credentials on this page you basically provide it to the attacker voluntarily, or more realistically, have been tricked into doing so. Most web developers will be able to build a fake website within a week of learning programming. It is a very simple but extremely effective method of harvesting credentials.
Phishing is a popular form of cybercrime because of how effective it is. Cybercriminals have been successful in using emails, test messages, direct messages on social media or even inside of video games and getting the victim to respond with their personal information. The best defense is awareness and knowing what to look out for.
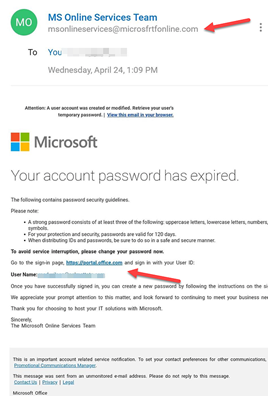
Here are some ways to recognise a phishing email:
Urgent call to action
Be suspicious of emails that advise you to click on a link or open an attachment. Often, they will claim that you have to act immediately to restore access to a service by requesting update to payment details or advise you to login to read a message on your account.
First time or infrequent senders
While it is not unusual to receive an email from someone for the first time, especially if they are outside of your organisation, this can be a sign of phishing. When you receive an email from someone you don’t immediately recognise take a moment to examine the message carefully before proceeding with any requests.
Suspicious links or unexpected attachments
If you suspect that an email is potentially a scam, do not open any links or attachments. It is good practice to hover your mouse over any links to see if it matches the link that was typed. In the following example the link attached to the text is revealed and clearly shows that it does not appear to be taking you to a company page.
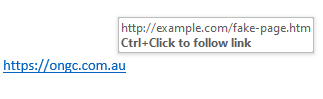
May be better not to use our website URL when illustrating a dodgy link
Often these fake links will take you to a replicated version of the website you intended to go to, but instead will be a fake page replicating the look and feel of the intended site in attempt to steal your credentials, often with a login page.
Absolute best practice, and a good habit to get into, is when you receive an email from your bank or a business requesting you to do something on their website. Don’t use the links in the email, instead navigate to the page manually by opening your browser and typing in the address you need to go to.
Incorrect email domains
If the email claims to be from a reputable company, like Microsoft or your bank, but the email is being sent from another domain entirely (for example; gmail.com or yahoo.com) it is likely a scam. Also be careful when assessing domains in the From line in emails as some scammers will replace letters with numbers or in place of the letter “m” use “r” and “n” (“rn”) next to each other to appear correct at a glance.
Cybercriminals have also been known to attempt to get you to visit fake websites with other methods, such as text messages or phone calls.
In summary if you ever receive a suspect email:
- Never click on any links in the email. If you receive a message from an organisation and believe that the request could be legitimate, go to your web browser and navigate there manually, either from your bookmarks or typing in the appropriate address.
- If the suspicious message appears to come from someone that you know, give them a call or get in contact by some other means to confirm the legitimacy of the message.
- Report the message as spam in your email application.
- Report the email to your Managed Service or IT provider
- Delete the message
If you suspect that you have inadvertently fallen victim for a phishing attack there are a few things you should do:
- While fresh in your mind write down any details that you may have shared, such as usernames, account numbers, or passwords.
- Immediately change the passwords on those affected accounts, and anywhere else that you might use the same email address and password combination. It is strongly suggested to use a password manager which will allow the use of complex passwords and ensure that there is a different password for every service you use.
- Turn on Multi-Factor Authentication (MFA) for every account and service it is available.
- If this attack is in any way related to your work or school account you should notify your Managed Service Provider or IT department immediately.
It is strongly recommended that your domain uses DMARC, DKIM and SPF records correctly as this will assist in preventing suspicious emails from appearing in your inbox at all. Also make sure that you are leveraging the most out of your email provider as there are several solutions available to increase your protection, for example, Microsoft 365 Defender.
If this is a topic that you would be interested in receiving more information on, or to learn how you can make sure that your business emails are as safe as possible, reach out to us either through our website https://ongc.com.au (don’t worry, this link is safe) or by phone 1800 664 248.





